DDos Attack: Types, Tools, Stop: Everything you Need to know
The DDOS attack is one of the Best attacks to down a web server or website. In this article, I will share everything that I know about DDoS attack.

No matter if you don’t know anything about it. I Will explain everything from scratch step by step
The DDoS full form is distributed denial of service. Using this you can’t you hack any website/web server but you can slow down the speed or even make it unavailable for some time.
Table of contents
What is DDoS Attack
Effect of the DDOS attack
Types of DDOS Attack
Tools for DDOS Attack
How to Run DDOS Attack against a website
How to Run DOS Attack against wifi
How to Bypass Cloudflare
How to Stop It
Other Resource to know more More about DDoS Attack
What is DDoS Attack in Actual?
DDoS is derived from dos (denial of service). So First we understand what is dos.
In a dos attack, a hacker sends traffic without any limitation to a particular web server or website. Look every website has some kind of limit to handle traffic.If any case limit exceeds that particular website/web server will down for some time. Here is a picture.
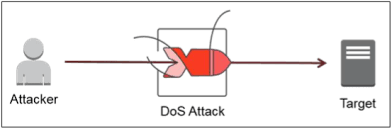
Now DDOs is distributed. This picture will give Idean about DDoS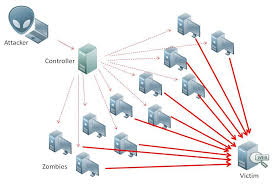

In DDoS either Hacker can you full Network (wif, or local network to which he connected) or he can create a virus and then install to millions of other computers.
Now, these millions of the computer under his control. in dos he has only one machine but in this almost unlimited.
Dos attack is easy to detect because only one computer is sending invalid traffic. You can block this. But in this case, you have no Idea.
Effect of the DDOS attack
The DDoS attack has always a negative effect on your website. Here are the main negative effects
Economic Damages
Speed is the most important thing in economic. If your visitors will face downtime or slow speed it will definitely affect your economic growth.
Your Image
Off curse, it will affect your image in the market. May your competitors can do this or any other person.
UnHappy Users
Types of DDoS attack
These are types of DDoS
Volume-based Attack
In this Hacker sends High amount of traffic to your web server or Request packets to overwhelm to its bandwidth capabilities. Generally, request size is between 100gbps 1tpbs.
It includes UDP floods, ICMP floods
Protocol Attacks
In this Hacker attack on layer 3 (Network layer) and Layer 4 (Transport Layer) by exploding a weakness. Use some feature of the protocol to launch an attack without being aggressive.
Here are layer 3 and 4 means OSI model layers.
examples SYN floods, fragmented packet attacks, Ping of Death, Smurf DDoS and more
Application Layer attack
In this Hacker attack top layer of OSI Model which is known as the application layer. In this common internet, request HTTP get/post occur. This is very difficult to detect. Because here it is difficult to Distinguishing between attacker traffic and normal traffic.
examples GET/POST floods, Slowloris Attack
Tools for DDOS Attack
Here are some best tools for DDoS that I find on the internet
Low Orbit Ion Cannon (LOIC): It is capable of sending mass amounts of ICMP or UDP packets to the target, thereby saturating the bandwidth, and has been used in some of the most effective and notorious DoS attacksHOIC: This is developed by the same developer who develops LOIC. But is the difference between them is that HOIC uses HTTP flooding. HOIC can dos upto 256 domain at once.
Slowloris: This is invented by Robert. it requires minimal bandwidth to implement. Basically, it works by opening multiple connections to the web server and try to open as possible it can do. It sends HTTP request but never complete the request
R.U.D.Y (R-U-Dead-Yet): THis tool is used to produce low and slow attacks. This is similar to the above tool slow loris. R.U.D.Y. sends a legitimate HTTP POST request with an abnormally long ‘content-length’ header field. It can be used to produce an application layer attack.
UDP Flooder: Full form of UDP is user datagram protocol. UDP is connectionless and sessions less protocol. Unlike TCP it does not require any three-way handshake.
However, these same properties also make UDP more vulnerable.
Pyloris: Pyloris is a slow HTTP DoS tool which enables the attacker to craft its own HTTP request headers. These include the packet header, cookies, packet size, timeout, and CRLF option. Pyloris is written in python language.
python SYN Flood Attack: To Understand this first you Need to understand what is syn Request. View this image to understand syn Request
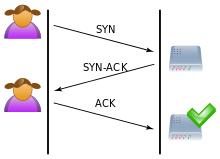
So it is a three-way handshake. Now Haker sends so many Request from this network to make server unavailable.
This is known as the syn flood. For this, you can python wrote syn flood attack.
How to Run DOS Attack against wifi
Using Hping3
hping3 is used to dos attack on web server mean it needs IP address. We will pass our router Ip address ( because the router is between every connection you made with the internet from any device). Here is command
hping3 -i u1 –baseport 80 -S 192.168.1.1
- Here is -i u1 define time interval (in milliseconds)
- –baseport 80 define port no. is 80 which is HTTP port if you don’t type any port then it will select random port.
- -S define attack should syn flood type.
- 192.168.1.1 is Ip address of our target machine.
How to stop a particular user INTERNET: at the end, I pass ip address of my router but if you replace it with victim IP address then it will stop that INTERNET of that user.
How to find the user Ip address
You can find router IP address using your router if you have router username and password (generally in wireless tab) or guess it
or
guess it with nmap. It is not that difficult look at your IP address type ifconfig wlan0 in my case it is 192.168.1. and IP address range is 192.168.1.1-256. You did not need to guess from all these we will use nmap to find which Ip address is up.
Here is command
nmap -vv 192.168.1.0/24 | grep “Nmap scan report for “
it will show host up ( mean connected devices IP address) as shown in the screenshot.
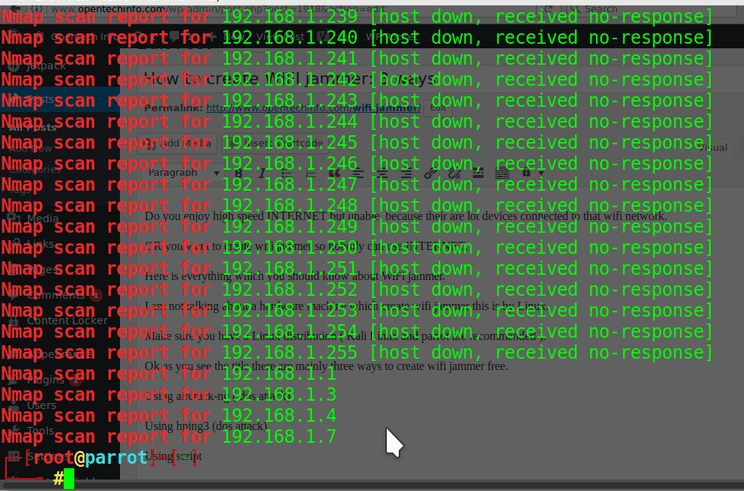
Now you need to guess one from it is your IP address type ifconfig to see your IP address 192.168.1.1 is gateway mean router IP address.
Guess the IP address and start dos attack in case if you want to stop INTERNET of a particular user.
Advantages
Guess the IP address and start dos attack in case if you want to stop INTERNET of a particular user.
Advantages
- you can stop INTERNET of a specific user
- simple commands w.r.t to aireplay-ng
Disadvantages
- Difficult in the case of if you want to target a specific user.
How to Bypass Cloudflare
If you study about DDoS then you know Cloudflare is the problem for you basically it is cdn service which also provides security from DDoS attack
Basically, it hides website real IP address and shows you Cloudflare IP address. But you can bypass it easily
How to Stop DDoS attack
web firewall: To stop application layer attacks you can use the web application firewall.
Call the Host provider: If you think that your website is under ddos attack can all your hosting provide and tell them that you are under attack
Call a DDoS mitigation specialist: If you have own web server then you can call a specialist. You can find on freelancer websites like upwork.com, fiverr.com etc.
OR you contact specialist like sucuri, Cloudflare, indusface
Edit Rate Limiting Rule: You edit rate limit rule like automatically block Ip address exceed 20 requests per minute.
Creating and detecting DDoS Attack using python
Conclusion
I hope you have learned something new from this article if you have any question then let me know by comments. I will happy to help you
Post a Comment